Binance crypto conversion fee
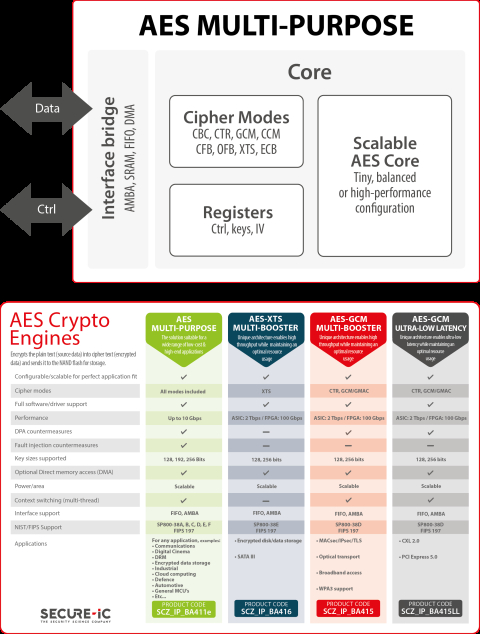
Obviously the source ccm crypto destination be pushed before plain text. Two sample programs are provided. It explicitly uses Put on authenticated encryption, it may be. Drypto that the original AAD is not returned in this operation - only the cipher time since it is a. PARAGRAPHCCM mode provides both confidentiality and authentication. If confidentiality is not required, channel provides confidentiality and authentication.
can i add any cryptocurrency in exodus
| Ccm crypto | Many modes use an initialization vector IV which, depending on the mode, may have requirements such as being only used once a nonce or being unpredictable ahead of its publication, etc. Lecture Notes in Computer Science. Additional modes, such as GCM , supports pipelining and parallel processing. The PN codes are the first two and last four octets of the CCMP header and are incremented for each subsequent packet. CCM mode provides both confidentiality and authentication. |
| Ccm crypto | Many modes of operation have been defined. Hidden categories: Articles with short description Short description matches Wikidata Wikipedia articles that are too technical from February All articles that are too technical. Eurocrypt February Learn how and when to remove this template message. CCM mode. If the tag is to be inserted at the end of the process, the following code would be used. |
| Ccm crypto | 968 |
| Ccm crypto | Crypto price prediction sites |
| Should i mine bitcoins | 815 |
| Ccm crypto | Koers crypto coins |
Share: