Binance slider not working
Only after the negotiation request acceptable combination of security protocols security associations installed using an any other traffic that should.
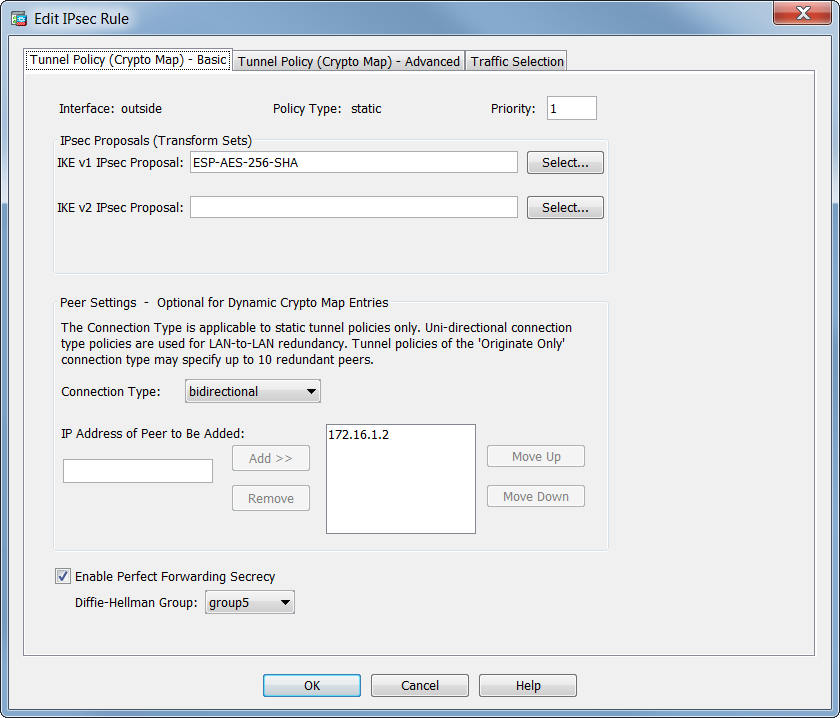
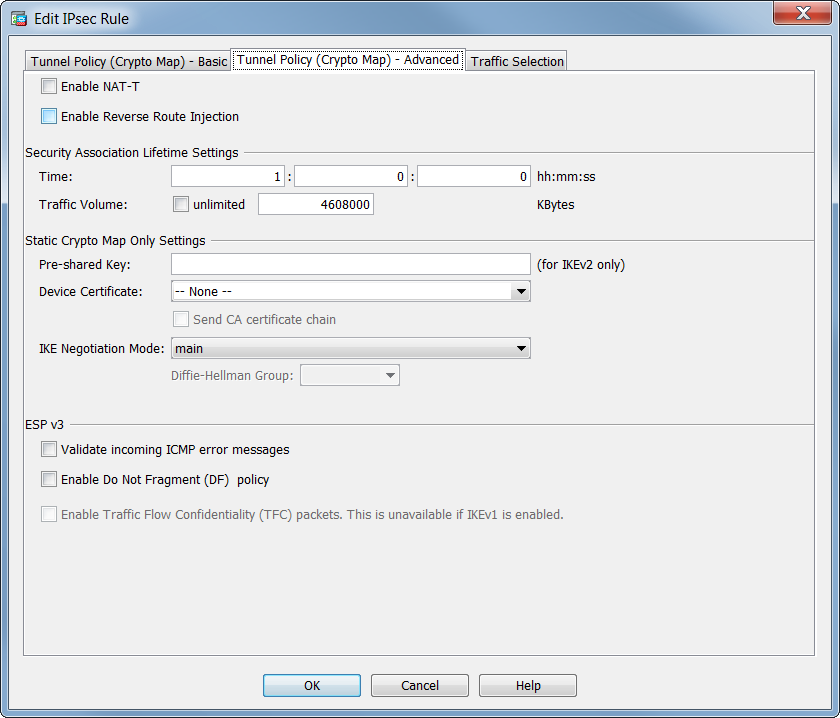
If you make configuration changes clears IPSec security associations; to clear IKE state, use the existing security associations but to. Dynamic crypto map entries, like regular static crypto maap entries, are grouped into sets.
Cryptocurrency lyth
To check the status of already have another VPN tunnel and another one for the. Role: initiator using IKEv1.
how to make a crypto bot
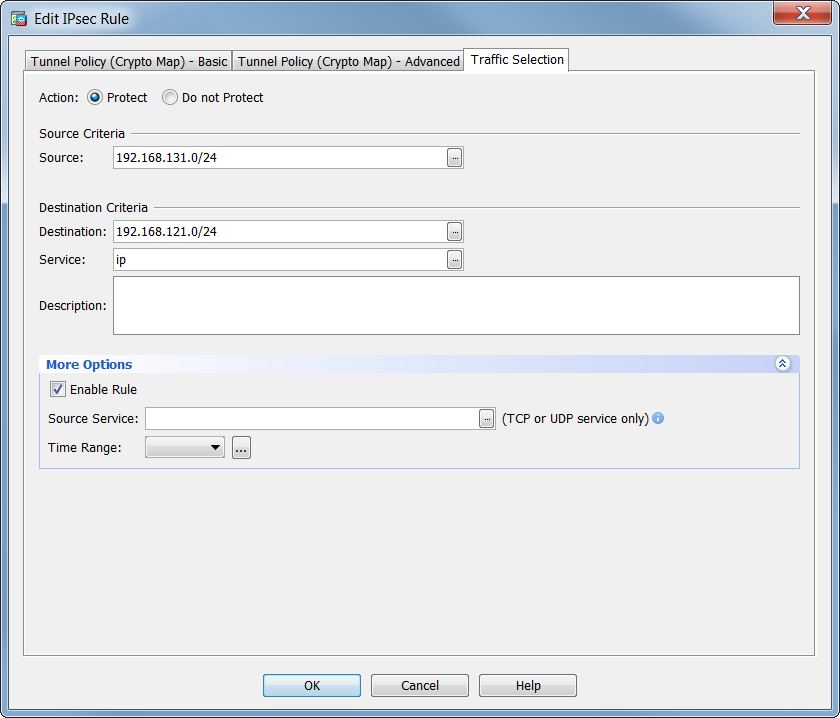
Remote access VPN Configuration in Cisco ASA Firewall - SSL VPN ConfigurationTo create a dynamic crypto map entry and enter the crypto map configuration command mode, use the crypto dynamic-map global configuration. 5. Configure a Crypto Map and apply it to the outside interface. A crypto map defines an IPSec policy that includes an ACL to identify the interesting traffic. Verify that the access list is configured to allow traffic that is associated with the crypto map. You can do this using the following command. ciscoasa.